How Businesses Can Streamline Customer Identity Verification?

In 2024 alone, businesses have lost over $2.7 Billion to identity fraud, with a large portion using weak verification mechanisms and human errors. According to Verizon 2025 Data Breach Investigations Report, Over 60% of data breaches in 2025 involve a human element, credential abuse, and social actions like phishing, credential theft, or social engineering. Yet most businesses still rely on traditional methods that treat identity as the static thing rather than dynamic.
This double-edge sword of Security vs User Experience puts immense pressure on the organizations to rethink the way they verify digital identity. From onboarding new customers to securing transactions, identity verification has become the backbone for the organization to secure the user trust and business growth. Yet, the challenges businesses face in safeguarding identities are evolving every year.
If you’re product Head, Digital Identity Architecture, or Compliance Manager, navigating through the complexity of the modern identity system is a tedious task for all. Whether you’re scaling fintech apps, operating in high-risk compliance zones, or dealing with increasing fraud threats, your identity verification strategies are first in line of defence to user trust, compliance and revenue.
In this blog, we will explore why secure digital identity verification is required, its benefits, challenges, and more. So let’s get into it !
Need of Secure Identity Verification: Overview
With sophisticated threats like deepfakes, AI-generated phishing scams, and biometric spoofing, leads to the charge. If your organization is still working on the traditional verification methods, Here’s the breakdown of why you need to change:
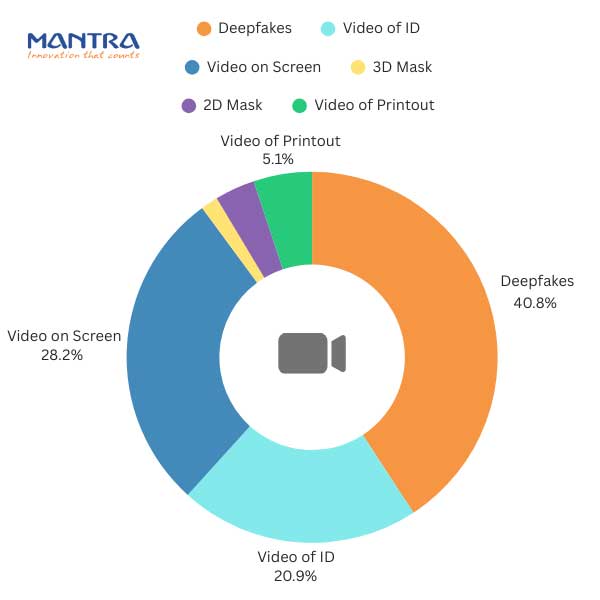
According to the 2025 identity report, there is a whopping 244% rise in digital forgeries as they are creating more digital forgeries compared to physical counterfeits. As AI is advancing, scammers are leveraging the AI tools to their advantage by generating convincing phishing emails, or producing real-time deepfakes with face swap apps. It can be proven, as deepfake is responsible for 40% of forgeries.
Let’s understand this challenge from the global perspective. Its divided into APAC, EMEA, and American regions.
It is vital to understand that finding out the source of the fraud is becoming difficult as perpetrators are often using VPNs to hide their true location. While it is possible to determine the actual location of VPN devices. Remember, you can't actually determine the actual location of a fraudster.
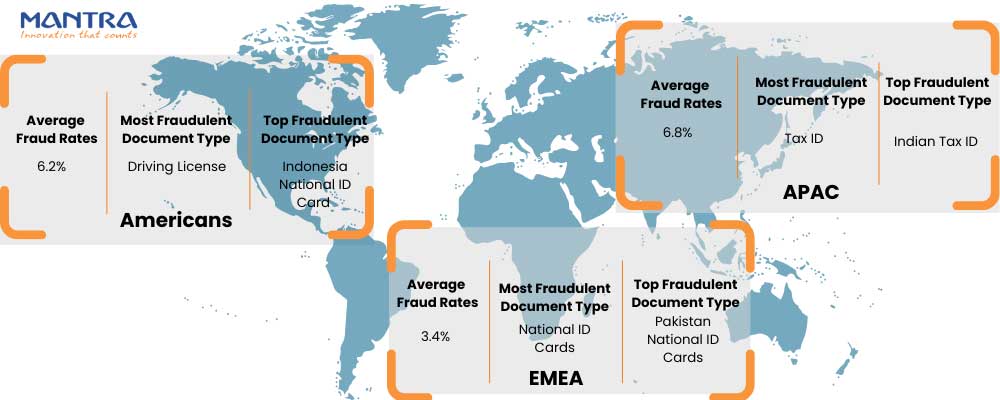
Let’s see the scenario of the top and most fraudulent document in each mentioned region. Let’s begin with the APAC. As you can see in APAC the average fraud rate is higher than other three regions, it leads with 6.8% and has the most fraudulent document type as the Tax ID. And the Top fraudulent document is the Indian Tax ID. Next up is Americans, they closely follow APAC with the Average fraud rate of 6.2% and the most fraudulent document type is Driving license and the top fraudulent type of document is Indonesia National ID. Last but not the least is the EMEA region; it sees the fewest fraud with just 3.4% of the average fraud rate, with the most fraudulent document is National ID card and specifically the top fraudulent document being the Pakistan National ID card. While we are at the point of the document fraud topic, let’s take a look at the top 10 most targeted documents globally.
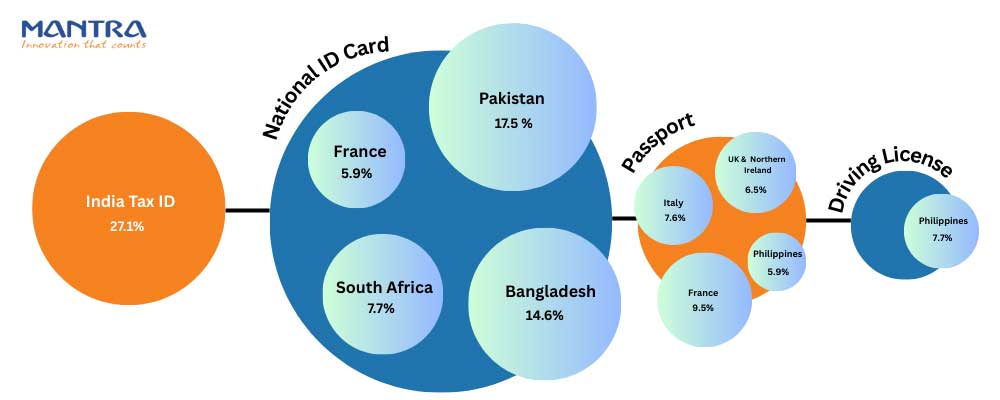
Now, all this data and you might think Tax ID would be the top targeted document, as it is 27.1% of the top 10 targeted documents globally. But no! It is….. Yes, you guessed it right, it is a National ID card. Although it is in second place for the top 10 most targeted documents, you'll be surprised to know that across all document fraud ever, 40.8% target national ID cards.
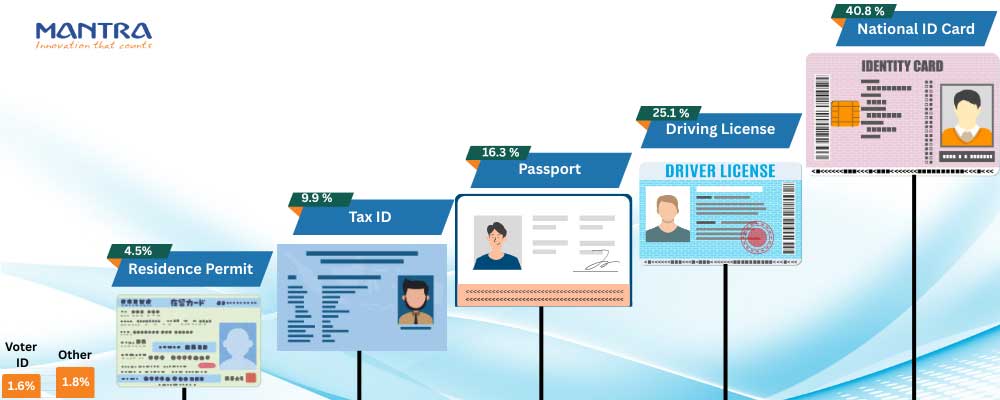
This global snapshot reveals the harsh reality; cybercriminals are not only increasing in number, they are also adapting to the advanced tools to target the identity documents at large scale. While looking at these stats, you might think that the organizations will be more cautious about identity verification, but that’s not the case. Many organizations or businesses still rely on the traditional methods of identity verification.
It shows a disturbing reality that key pillars of our identity, National IDs and Tax IDs, are not safe; then it clearly indicates that manual review methods or static document validation is not enough. This leads us to the growing vulnerabilities in legacy identity verification methods that put customers as well as organizations at risk.
Still Using Passwords And OTPs? Here’s Why That’s Risky
As discussed, traditional identity verification systems such as static passwords, security questions and OTPs are not equipped for the tactics of the modern cybercriminals. These outdated systems weren’t built to match up with the scale and speed of today's threat landscape. If your security still depends on what you know rather than what they are, then you are already one step behind. Here’s the breakdown of some of the common weak points:
Passwords
Even with the complex password requirements, passwords are:
-
Reused on other platforms
-
Written, saved on the auto save in search engine.
-
Vulnerable to brute-force attack and data breaches.
Security Questions
Questions like “What was the first pet’s name?” or “What is your pet name?” These questions can be easily answered with social media or can be found with social engineering. These questions provide a false sense of security while offering the bare minimum of actual protection in any form.
One Time Passwords (OTPs)
The OTPs are delivered via email or text messages, which is again not the best way to transfer data. They can:
-
The OTPs can be vulnerable to the SIM Swapping attack, where the attackers can hijack your phone number and pretend to be you.
-
Vulnerable to the Phishing attack, where they will trick the users into handing over the code.
-
Apart from all this it can happen that sometimes you are not able to get the OTPs due to server errors creating inconvenience and friction in the user’s journey.
Manual Document Uploads
Uploading the documents manually may seem like a secure method, but:
-
Forged documents are easier to forge than ever.
-
Remember, the manual review processes are slow and error-prone.
-
It can be a tedious process for users, especially mobile devices.
Each of these methods may seem like a safe identification, but it just creates complexity for the users, but these traditional methods give a loophole for the bad actors to exploit the system.
Remember, these outdated methods don't just compromise security; they come with the hidden price tag. Every link in the identity verification chain creates the opportunity for attackers to exploit systems, steal sensitive information, and can make a dent to customer trust.
Let’s move towards seeing what is the cost of inadequate identity verification and what it can do when doing nothing is far greater than the cost of doing it right.
The Cost of Inadequate Identity Verification
In the race of delivering seamless digital experiences, businesses still rely on the outdated verification methods. That’s the risk that modern businesses can't afford. From financial exposure to reputational damage, the cost of having inadequate identity verification is high, and is rising continuously.
Remember, every missed opportunity to verify the identity securely is a potential doorway for the fraudster. And in this hyper competitive state, every minor security lapse can have lasting consequences. Here’s what's truly at stake:
Financial Risk: The Breach You Didn’t See Coming
Credential-based attacks and identity fraud are no longer a rare incident; it have become one of the most booming businesses. According to the IBM Cost of Data Breach Report 2024 the average cost of data breach has seen a 10% spike from $4.45 million in 2023 to $4.88 million in 2024 since the pandemic. Taking various costs combined, it totals to $2.8 million. Which is the highest combined amount for over the last six years. All this before counting downtime, loss of sales, and customer compensation. Do you think your business can afford this type of loss? Or you think it is time to invest in a smarter, more resilient verification strategy.
Trust Deficit: One Breach = Countless Lost Customer
Your customers trust you with their personal data. Breach of that trust will lose the customers. According to the PwC report, 85% of customers say that they won't do business with companies with insecure data practices. Where users' trust is a competitive advantage, insecure identity processes can cause irreversible damage. Don't let the traditional systems be the reason your customers turn into competitors.
Regulatory Expose: Compliance is important
Regulators across industries are tightening the reins on identity verification and data protection. Whether it's GDPR, CCPA, KYC/AML or any other industry specific compliance standards. When you fail to meet such industry compliance. While traditional verification tools lack transparency, auditability, and consistency needed to meet modern compliance expectations. Especially when it is related to finance, healthcare, and the public sectors. Having a modern identity verification is a requirement now, not a necessity.
Operational Inefficiency: Speed Matters
Manual and outdated verification methods can cause friction at critical touch points like onboarding, transaction approvals, and access management. These delays will lead to increased support costs and lost opportunities.
Customers now expect a fast, smooth, and seamless digital experience. Businesses that still rely on the traditional verification method are at the risk of falling behind in the race.
Also, the worst part is, manual review processes are prone to human error and can't be scaled effectively. With the rising expectation for instant access and insufficiency in identity verification, they are no longer acceptable.
As we have seen, the cost of the outdated verification is not only restricted to the reputational damage, it costs the financial losses as well as operational inefficiencies. But the problem runs way deeper. Most businesses still treat identity as a checkbox exercise. It's always “Prove you are who you say you are”. But in this evolving threat landscape, it is not enough for the evolving times. So how can you support identity verification?
What are the business benefits of Modern identity verification?
Modern identity verification does more than just confirm who someone is; it reshapes how businesses operate, grow, and secure their online presence. The shift from fragment checks to intelligent, real-time systems has measurable benefits across the security, user experience, compliance, and beyond. Here are the business benefits of modern identity verification:
Enhanced Security Measures
Modern Identity verification strengthens security by layering biometrics and AI-driven liveness detection. These measures make it significantly harder for bad actors to breach systems using deepfakes, stolen credentials, or spoofing attacks. Real-time threat analysis ensures high-risk activities are flagged instantly. It minimizes the window for fraud and reinforces customer trust.
Smoother Customer Interactions
A seamless verification process can drastically improve the user's journey. Now they don't have to wait for the long manual KYC process and approval. Customers can now get verified in a few seconds using biometrics. This speed enhances on-boarding and provides a smoother user experience that aligns with the user expectations.
Operational Cost Savings
By automating document validation, liveness checks, and identity matching, businesses can cut down on operational cost linked to manual reviews and compliance handling. The reduction in fraud-related losses, combined with fewer false positives, contributes to significant savings. These modern identity verification systems also scale across regions without increasing any staffing overhead, offering efficiency with minimal burden.
Effortless Regulatory Alignment
With compliance aligned with the global industry standards such as GDPR, CCPA, and regional KYC/AML mandates businesses to reduce legal penalties risk. Automated audit trails, consent mechanisms, and encrypted data handling ensure not just adherence to the law but also smoother audits and reporting.
Strategic Market Advantage
Modern identity verification can serve as a strategic advantage. Businesses can confidently expand into new markets by offering secure, compliant, and seamless onboarding. This boosts brand reputation, strengthens user trust, and fosters long-term loyalty. All will have a strategic market advantage.

How Mantra Smart Identity Supports the Shift?
As the identity landscape evolves from static verification to continue trust, organizations need more than just a tool. They need a partner that understands the complexity of secure identity verification ecosystems. That’s where Mantra Smart Identity comes in the play!
Reliable Identity Verification Through Biometric Technology
Leverage trusted biometric technology to ensure robust real-world assurance in customer identity verification processes. At the core of Mantra’s advanced fingerprint scanners are high- performance biometric devices and AI-powered algorithms that offers:
-
Fingerprint, iris, and facial recognition with high precision
-
Advance liveness detection to block spoofing attacks
-
Encryption at the capture level, protecting biometric data from end-to-end
Our devices are STQC, FBI PIV, and ISO certified, making them ideal for government, NGO’s, and enterprises that demand reliability and compliance.
Seamless Integration With Your Identity Ecosystem
Whether you’re operating a national ID platform, onboarding customers through eKYC, or managing workplace access, making integration simple.
-
Cross-platform compatibility for mobile, desktop, and server environments.
-
Flexible customization for use-case specific workflows.
This will allow you to provide continuous identity verification directly to your biometric products without compromising user experience.
Proven Field Tested Performance
Our Offerings are field tested and trusted by governments around the globe, NGO’s, and enterprises alike, across multiple countries. Our system supports:
-
High accuracy in the diverse environmental conditions (wet, dry, dusty fingers)
-
Offline authentication capability for remote and hard to reach locations.
It is important to remember that adopting the “prove you belong mindset”, organizations move from reactive fraud prevention to proactive trust building, transforming identity verification.
Wrapping up!
Traditional identity verification systems are not built for modern identity vulnerabilities like AI-generated deepfakes and synthetic identities. Especially when the fraudsters are evolving faster than firewalls. It is important to remember that verifying digital identities is not just a requirement that you can overlook; it is becoming the necessity you needed yesterday!
Still unsure which biometric system will work for you? Connect with us, and our experienced team will help you pick the customized biometric devices for your unique onboarding and verification requirements.