Fingerprint Minutiae Demystified: Key To Reliable Biometric Matching

Have you ever thought about why all our fingerprints are different? How does every person have unique fingerprints the same as a snowflake? It’s astonishing that even twins don't have the same fingerprints. Therefore, fingerprints have long stood as the most used biometric modality worldwide. But what makes fingerprints unique?
At the heart of fingerprint recognition is the concept of Minutiae. But what is minutiae? It is the tiny microscopic ridge patterns that make your fingerprint unique. This blog will take a deep dive into understanding minutiae and why it is important to detect spoof detection, as many high quality spoofs such as 3-D fingerprint molds can replicate minutiae and Liveness Detection is required to counter this.
What Are Fingerprint Minutiae?
Fingerprint Minutiae are the tiny microscopic ridges and characteristics that form the backbone of fingerprint recognition systems. These tiny, yet highly distinctive features make every fingerprint biometrically unique, even among identical twins. While general ridge flow may appear similar, but the location, direction, and relationship of minutiae is what makes it different from the million other prints present.
Types of Fingerprint Patterns & Fingerprint Minutiae Characteristics
Did you know? An average full fingerprint contains over 150 unique ridge characteristics, each forming the intricate pattern
Loops
Arches
Whorls
Loops
Loops are the majority of the fingerprint patterns, with 65% of the fingerprint patterns found.
But how do you know the fingerprint is a loop?
A loop must have one or more ridges entering from one side of the print, recurving, and exiting from the same side. Here are three things that you should know about loops:
It must have a sufficient curve
It should have a delta
There should be enough ridge count and a looping area
There are two types of loops in the fingerprint pattern: Ulnar and Radial
1. Ulnar Loop
If the ridges enter & exit towards the little finger, it is called an Ulnar loop.

2. Radial Loop
If the ridges enter & exit towards the thumb, it is called a Radial loop.

It is important to remember that loops should have 1 delta!
For better understanding, we can say that the direction of the loop, be it Ulnar or Radial, can be determined by the ridge flow relative to the hand’s bone, not just the position. A loop is Ulnar if the ridges flow towards the ulnar or little finger. And the loop is radial if the ridges flow towards the radius (Thumbs). It can occur on either hand. While working on a case or looking at fingerprints, it is important to know what hand it is to determine whether it is Ulnar or Radial.
Arches
An arch is a pattern where friction ridges enter on one side, rise in the center, and then exit on the other side. Arches are characterized by smooth wave-like ridge flow and lack the loops and whorls of the other fingerprint patterns. There are two types of Arches:
1. Plain Arch
Plain Arch is formed by ridges entering from one side of the print, rising & falling, & exiting on the opposite side just like a wave!

2. Tented Arch
The tented arch is similar to the plain arch except that instead of rising smoothly at the center, there is a sharp upthrust, or we can spike, on the ridges that meet at an angle that is less than 90 degrees.

It is important to remember that Arches don’t have type lines, deltas, or cores.
Whorls
These are the 30-35% fingerprints found in the world and are divided into 4 subdivisions.
Plain Whorls
Central Pocket Loop Whorl
Double Loop Whorl
Accidental Whorl
Let’s understand each one of these in detail:
1. Plain Whorls

Technical Definition:
A plain whorl is a pattern which consists of one or more ridges which makes or tends to make a complete circuit, with two deltas between which an imaginary line is drawn. And at least one recurving ridge within the inner pattern area is cut or touched.
In Layman Term:
Plain whorls are the type of whorls that consists of one or more friction ridges making a complete circuit and two deltas. But how would you understand that it is Plain Whorls?
Let’s understand what characteristics make it plain whorl.
Find 2 deltas
Draw a straight line between 2 deltas
The rule is any ridge pattern that goes in the circular pattern inside. If even one of them crosses the straight line & comes back due to a circular pattern, it is known to be the plain whorl pattern.
Remember, no other whorl will follow this behaviour.
2. Central Pocket Loop Whorl

Technical Definition:
A central pocket loop whorl consists of at least one recurving ridge, or an obstruction at right angles to the line of flow, with two deltas, between which when an imaginary line is drawn, no recurving ridge within the pattern area is cut or touched.
In Layman Term:
A type of print pattern that has two deltas, and the imaginary line between 2 delta doesn’t touch or cross any of the ridges making the circular pattern in the middle of the print.
Let’s understand what characteristics make it Central Pocket Loop Whorl.
Find 2 deltas
Draw a straight line between 2 deltas
The Imaginary line between two deltas must not touch or cross any recurving ridge in the inner pattern
3. Double Loop Whorls

Technical Definition:
A double loop whorl consists of two separate and distinct loop formations with two different cores and two different deltas. The word separate, as used here, doesn't mean unconnected. The loops can be connected by an appending ridge if it doesn't touch at right angles between the shoulders of the loop formation.
Remember, To count as a double loop fingerprint, there must be two clearly separated loops.
This rule means we don't consider patterns like:
An “S” shaped swirl
Two loops twisted in one (interlocking loop)
One loop inside another
All of these might look fancy, but they don't meet the technical definition of the double loop. Each loop in a double loop must stand out on its own.
In Layman Term:
These fingerprint types have two loops side-by-side, with one loop parallel to the next. For easy understanding you can imagine the Ying & Yang sign.
Remember, Whorls offers a number of tracing as well. They are:
Inner Tracing
Outer Tracing
Meet Tracing
Let‘s understand each of these tracing patterns.
Outer Tracing : If there are 3 or more intersecting lines and they are outside of the pattern area, it is called Outer Tracing
Meet Tracing: If the number of intersecting lines are three or less, then it is called Meet Tracing.
Inner Tracing : If there are 3 or more intersecting lines and the intersecting point is inside the pattern area, it is called Inner Tracing.
Now that it is clear, let’s move towards the accidental Whorl.
4. Accidental Whorl

Technical Definition:
Accidental whorls consist of a combination of two different types of patterns, with two or more deltas or a pattern which possess some of the requirements for two or more different types of patterns which confirms to none of the definition.
In Layman Term:
Basically, it's a fingerprint that combines two or more fingerprint types. Or it is just a different fingerprint that does not match any fingerprint definition.
Now that we have understood the different types of Minutiae, let’s understand the different characteristics of minutiae and its extraction methods
Fingerprint Minutiae Characteristics
Now this is about the fingerprint patterns. Let’s talk about Fingerprint Ridge characteristics now. There are multiple Fingerprint Minutiae. Here’s the breakdown of a few of them:
Ridge Ending
Bifurcation
Dot
Island / Short Ridge
Lake (Enclosure)
Hook (Spur)
Bridge
Double Bifurcation
Trifurcation
Opposed Bifurcation
Ridge Crossing
Opposed Bifurcation ending

How Minutiae Points Are Extracted?
Minutiae points, which are the characteristic ridge formations in the fingerprints, are extracted through a process involving a sequence of image enhancement and feature detection techniques that can convert a raw fingerprint into a refined set of unique data points for biometric matching. Here’s the breakdown:
Input Fingerprint
The process begins with capturing the fingerprint image using the biometric fingerprint scanner. The initial image is likely to contain noise, uneven contrast, or artifacts caused by skin texture, pressure, or environmental conditions.
Smoothing
The raw fingerprint undergoes smoothing to reduce noise and enhance the continuity of the ridge patterns. This helps in producing clearer ridges and furrows, making it easier to distinguish significant features later in the process.
Binarization
Once the image is smoothed and converted into the binary format,(although modern algorithms such as deep learning often skips binarization/thinning process. Grayscale based methods directly extract minutiae) typically black & white, through a process called binarization. In this step, ridges are presented in black and valleys are shown in white. This simplification may look like a small thing, but it is crucial for the further process.

Thinning
Once the image is binarized, it is then thinned, reducing the width of each ridge making it a single line pixel. Thinning ensures that the geometric structure of the ridges is maintained while making it computationally easier to detect minutiae.
Minutiae Extraction
Once the fingerprint image is thinned, the algorithm scans the ridge skeleton to identity minutiae points, such as:
☆ Ridge endings (where a ridge terminates)
☆ Bifurcations (where the ridge splits into two)
These detected minutiae are marked on the fingerprint image, indicating key locations for matching.
Remove False Minutiae
To ensure accuracy, a false minutiae removal step is implemented. Some points may be incorrectly identified due to noise, broken ridges, or smudges. This step filters out such artifacts, retaining only valid minutiae for reliable biometric matching
How To Extract Minutiae From Fingerprints?
Fingerprint recognition relies heavily on the minutiae. Specific ridge characteristics like endings and slips that help verify someone’s identity. But to identify these points accurately, there is a need for effective minutiae extraction techniques. These methods vary based on the type of fingerprint image being processed. Here are some of the methods:
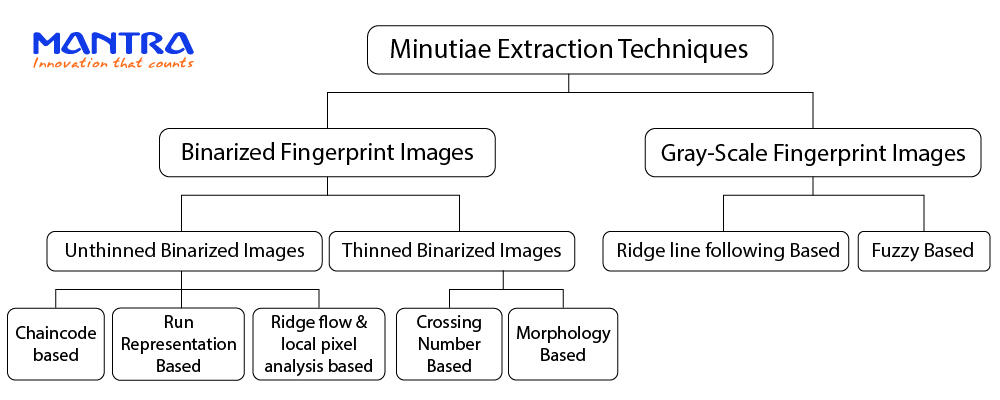
Binarized Images
Binarized Fingerprint Image Techniques
When it comes to fingerprint recognition, everything starts from Minutiae. Those tiny, unique features like ridge endings and bifurcations that make your fingerprint yours again. But how exactly are these details pulled out of an image? The process is called minutiae extraction, and it is more complex than you can imagine! Let’s see how.
If you’ve never wondered how fingerprint scanners manage to capture such a precision, the diagram above gives a great overview. It splits the techniques into two big categories Binarized Fingerprint Images and Gray-scale Fingerprint Images. Let’s walk through what that means in simple terms.
Working with the Binarized Fingerprint Images
In this method, fingerprint images are first converted by binary form. Typically black-and-white, where ridges and valleys are distinctly separated, nothing in between. These are further processed using either unthinned or thinned image-based techniques:
1. Unthinned Images:
These fingerprint extraction methods approach extract minutiae directly from the binary images without thinning. This preserves the ridge and the original ridge shape, avoiding distortions introduced by thinning algorithms.
1.1 Chain Code-based Extraction
Chaincode are directional representations of contours around fingerprint ridges.
Each ridge is encoded as a sequence of directional vectors (e.g 0-7 in freeman chaincode)
Changes in the direction or breaks in the community indicate the presence of minutiae.
🔎Use Cases: Chain code-based extraction is generally ideal when fingerprint ridges are clearly defined.
⚠️Be Vigilant About: Chain-based technique may misinterpret the ridge breaks caused by noise as minutiae.
1.2 Run Representation-Based Technique
The image is analyzed row-by-row or it can be column-by-column, and each continuous black pixel segment is termed as ‘run’.
A run is interpreted as a segment of a ridge.
Minutiae are detected at the start of or at the end of these runs. It can also happen where the multiple runs tend to meet or separate from another route and go in different directions.
🔎Use Cases: Run-representation based is suitable for fingerprint images with consistent ridge widths.
⚠️Be Vigilant About: Run-representation lacks precision in areas of curve or ridge crossover.
1.3 Ridge Flow and Local Pixel Analysis - Based Techniques
This technique focuses on understanding how ridges flow within the local windows of the images.
Techniques such as orientation field estimation and flow direction maps are used to detect the anomalies or any changes. All this indicates the possible minutiae.
🔎Use Cases: Ridge Flow technique is better for the fingerprints with curvature and pattern variation.
⚠️Be Vigilant About: This technique requires robust preprocessing and ridge enhancement.
2. Thinned Binarized Images
Here, thinning or skeletonization is applied to reduce ridge lines to a width of one pixel. This signification simplest the task of locating minutiae by making ridge endings and bifurcations easily identifiable through pixel connectivity.
2.1 Cross Number (CN)-Based Techniques
Cross number based techniques is one of the widely used techniques.
It involves calculating a “cross number” for each pixel in a binary image to identify and classify feature points.
The number of 0-1 transitions in the 8-connected neighborhood determines if the point is a ridge ending (CN=1) or bifurcation (CN=3)
The minutiae is extracted using 3*3 pixel window is moved across the image.
🔎Use Cases: Cross number based technique is highly efficient for real-time or embedded systems.
⚠️Be Vigilant About: This technique requires clean, noise-free thinning to avoid any false minutiae.
2.2 Morphology-Based Techniques
Applies morphological operations such as dilation, erosion, skeletonization to refine ridges and remove the noise.
After filtering and smoothing the image, structural patterns are analyzed to extract minutiae based on shape, continuity, and geometry.
🔎Use Cases: Morphology based technique works well with irregular ridge structures or broken lines.
⚠️Be Vigilant About: In this technique, parameter tuning is critical for avoiding loss of valid minutiae.
Working with the Grayscale Fingerprint Images
Unlike the methods from above, these techniques bypass binarization and operate directly on the grayscale image. This preserves the natural information in the image, making them better suited for latent, partial, or smudged fingerprints commonly encountered in forensic scenarios.
1.1 Ridge Line Following Based Techniques
The ridge line algorithm traces the ridges by identifying paths of highest intensity contrast.
By “Walking” along with these ridge lines, the algorithm detects points where ridges terminate or split indicating minutiae.
🔎Use Cases: This Ridge line following technique is effective for latent or low contrast images where binarization would obscure the detail.
⚠️Be Vigilant About: This technique is sensitive to smudges and requires high precision control logic.
1.2 Fuzzy Logic-Based Techniques
Introduces fuzzy membership functions to handle ambiguity in pixel intensity and ridge shape.
Each Pixel is assigned a degree of belonging to the ridge or valley.
Minutiae are extracted based on the combination of fuzzy rules that model ridge terminations and bifurcations under uncertainty.
🔎Use Cases: This Fuzzy logic based technique is extremely useful in forensic & forensic matching scenarios.
⚠️Be Vigilant About: This technique has complex implementation and is slower than rule-based methods.
Choosing the Right Minutiae Extraction Techniques
The best Minutiae technique depends on multiple factors. Here’s the breakdown of them:
Quality of Input: Is the image provided as input clean, partial, smudge or is it latent?
Application Context: For what context are you looking for a minutiae extraction method? Is it for eKYC then requires speed, is it for forensic? Then it would require accuracy.
System Resources: What are the system resources for which you’re looking for an extraction method? As real-time systems require lightweight algorithms, whereas cloud-based systems can afford the deep learning mechanism.
It is important to remember that biometric solution providers often integrate multiple biometric modalities and multiple methods. For e.g using ridge enhancement followed by CN or morphology for initial extraction, then refining with an AI-Based filter. But here the question also arises that what advantage is there with matching biometric minutiae? Let’s figure it out!
What are the Benefits of Minutiae in Biometric Matching?
Fingerprint recognition systems do not compare the complete images; instead, they rely on comparing the minutiae points. These comparisons include:
Orientation Ridges
Types of Minutiae
Relative position
Distance & angle between neighbouring points
Because these parameters are unique and difficult to replicate, minutiae based matches ensure strong resistance against spoofing and impersonation.
Benefits of Minutiae-based Matching
High accuracy and low false acceptance/rejection rates.
Compact data storage, enabling faster processing
Resilience to partial prints, as even a few minutiae can suffice
Scalability suitable for national ID databases or large-scale systems.
What challenges are faced in Minutiae Matching
While it is important to know that minutiae based fingerprint matching is considered to be the most reliable biometric techniques, as with any other technology, they also don't come without their challenges. There are several factors that can compromise the accuracy, efficiency, and robustness of minutiae matching.
Low-quality Fingerprint Scans
It is not mandatory that you’ll get the best quality fingerprint always. Might there be poor quality fingerprints caused due to the dry, wet, or scarred fingerprint can cause a lot of noise and disturbance in producing the complete ridge patterns. This can lead to the missed or falsely assumed minutiae points. It can make the minutiae matching process less accurate.
Partial Fingerprints
In use cases like border control or time attendance systems, you might get partial fingerprints. It can be the reasons because of the insufficient space on the scanner or due to the improper fingerprint placement. With the partial fingerprint, the number of minutiae points will also decrease for the comparison, affecting the confidence in the matching.
Non-Uniform Pressure
Excessive or uneven pressure during the fingerprint capture can distort the ridge patterns, stretching or compressing minutiae. This nonlinear distortion complicates accurate matching, especially in sensitive security applications.
Variations in Finger Orientation and Position
Fingerprints that are captured from different angles or positions can result in rotated, translated, or flipped patterns. Without any robust alignment algorithms, matching algorithms may fail to find corresponding minutiae.
False Minutiae
Noise introduced during preprocessing can create false minutiae points. These points appear as ridge endings or bifurcation but don't actually exist. These false points are needed to be carefully vetted out to avoid any false matches, affecting the integrity of minutiae matching.
Template Size & Speed Trade-off
Minutiae based templates are generally compact, but can have a big size. Therefore, using them to match against any large databases such as national ID systems can lead to increased computational time. It is important to maintain the balance between accuracy & speed as it remains a constant trade-off.
Spoofing & Presentation Attack
Fake fingerprints made using materials like silicon, gelatin, or 3D printing can mimic real minutiae structures. If the system lacks robust liveness detection or spoof detection, it may fail to distinguish genuine users from spoofed ones.
How Mantra Smart Identity Enhances Minutiae-Based Matching?
At Mantra Smart Identity, our biometric device like MELO31 is engineered to capture fingerprints with exceptional clarity and accuracy, enabling superior minutiae extraction even in challenging conditions. These fingerprint sensors are equipped with the scratch resistant surface, high-resolution sensors, and certified liveness detection, our fingerprint scanners are built to support:
Scalable national ID systems
Border security checkpoints
Voter registration programs
Financial and health authentication platforms
Our commitment to quality ensures that each captured fingerprint delivers pierce minutiae for dependable identification, regardless of age, location, or condition.
Minutiae: The DNA of Fingerprint
Fingerprint Minutiae are the heroes of biometric recognition. Their unique, stable, and fine-grained nature makes them the foundation of reliable identity verification. As biometric systems are evolving, minutiae based matching continues to offer a balance between security, speed, and scalability. It is important to understand and leverage fingerprint minutiae as it is key to build the trust in biometric systems for government programs to enterprise-grade access control.